Cybersecurity Standards
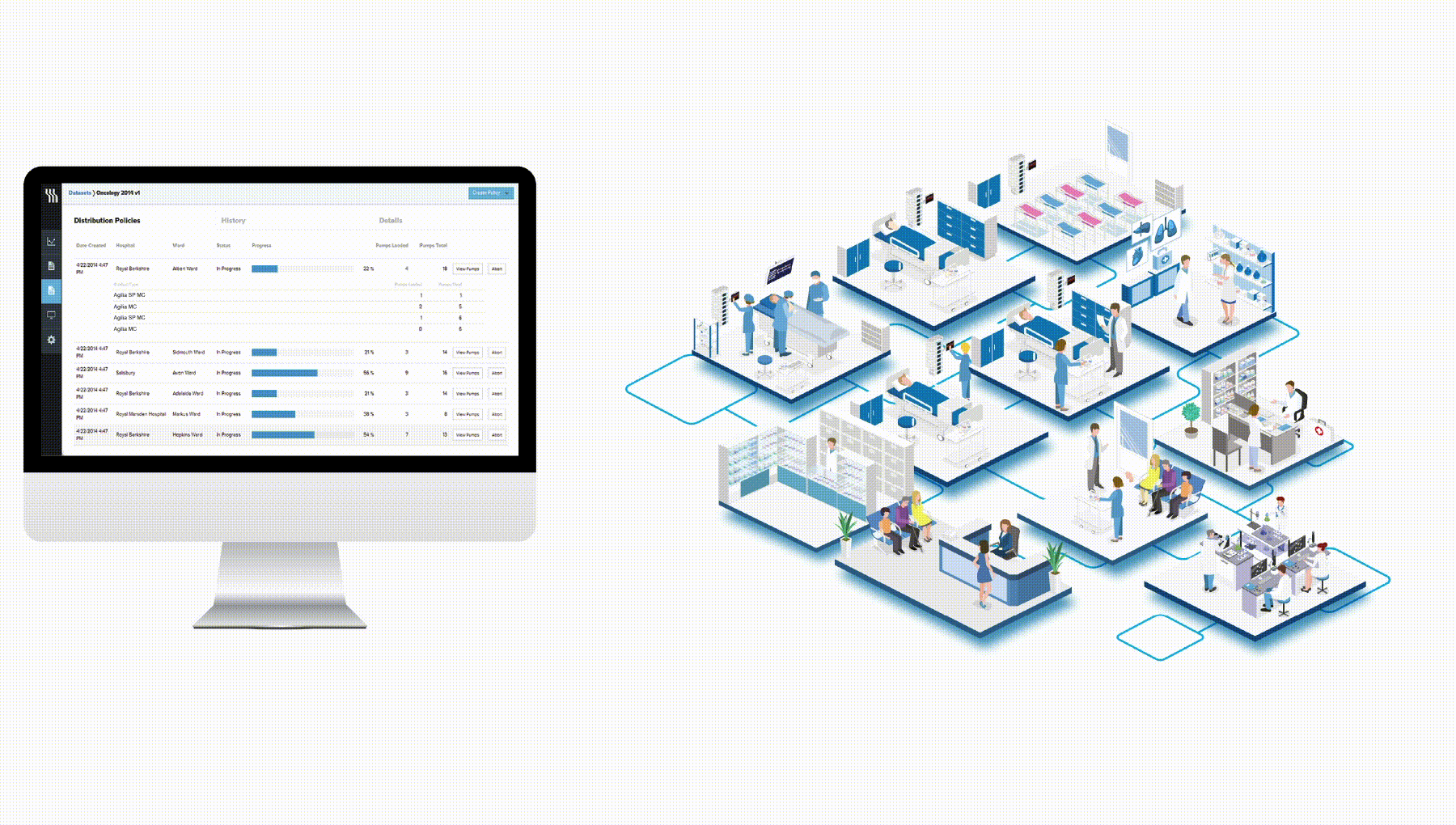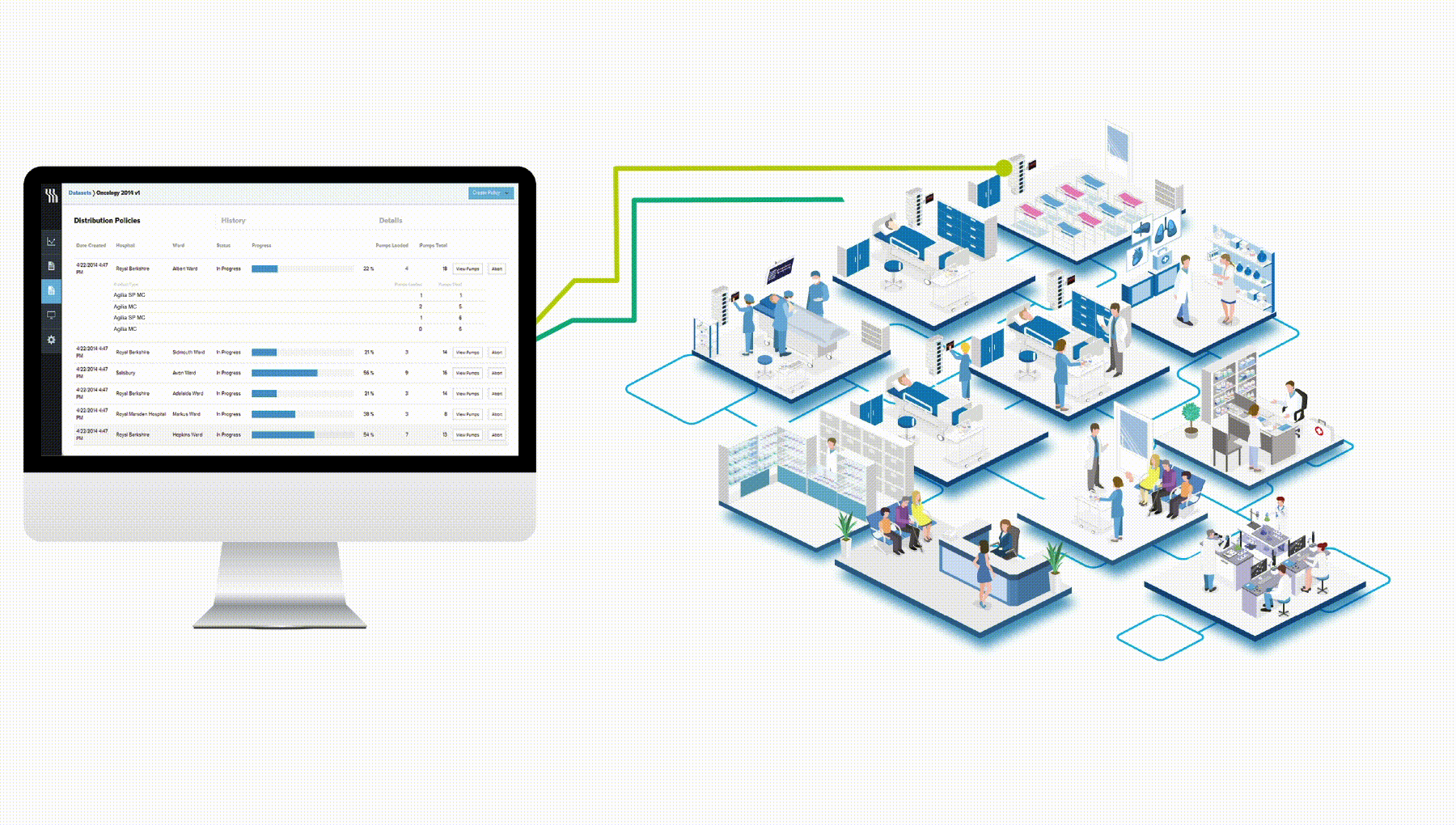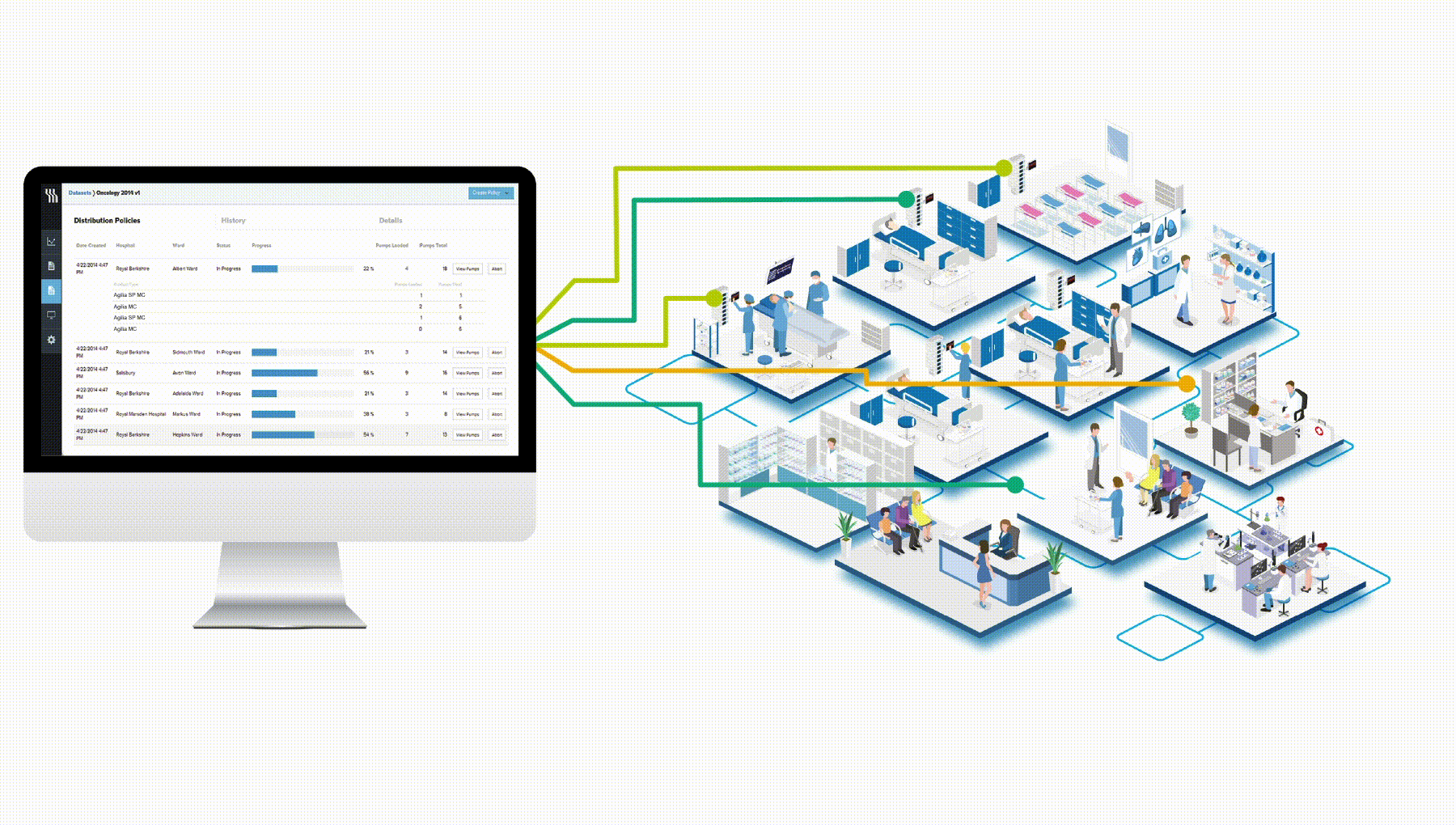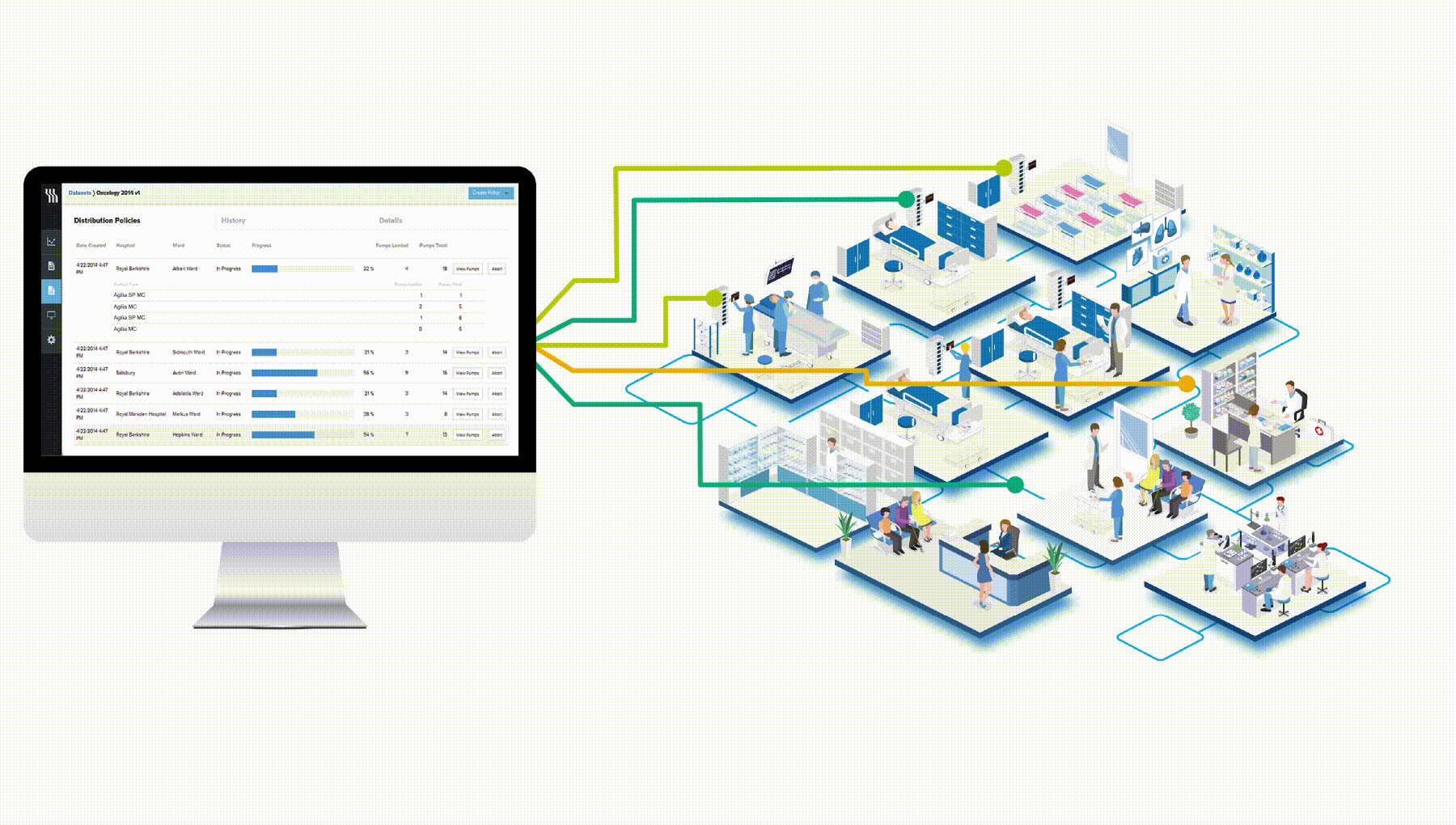
Centerium can only be installed through a licence distribution system maintained by Fresenius Kabi Support Centre and is protected by an isolated firewall policy with no listening port open on the internet.
VSS is a server-based solution using Microsoft solutions:
All dataflows between VSS components are encrypted/verified using:
Digital
certificates


Allow strong authentication and encryption to provide secured communication within our system and with external ones.
Preshared
Keys


The Secured key sharing system ensures that no device enters the system without control for a secured fleet management.
VPN


Establishing a VPN connection between docking stations and the server ensures efficiency because performance and segmentation are essential.
Agilia Connect System has been evaluated by Cigital/Synopses, one of the world's largest application security firms, using the NIST 800-30 standards and is found to mitigate many vulnerabilities by:
- Physical separation of pump devices from wireless modules
- Unique security keys for individual pump device
- HMAC authentication for bi-directional communications of pump
- Independent primary pump operations that remain undisrupted by software updates and data traffic through wireless module
Proactive Assessment and Surveillance
Following ISO/IEC 29147, Fresenius Kabi has integrated cybersecurity requirements into the related pre- and post-market quality management systems procedures, including risk management, and proactively evaluates field feedback from customers, public advisories from health authorities, updates of standards and publications from national institutions, e.g. CERT.
A monitoring of security information takes place on an on-going basis for all the Fresenius Kabi products. Any cybersecurity vulnerabilities affecting Agilia Connect System that are published by cybersecurity workgroups, detected by hospital IT-security management, or in-house regular penetration tests, are funneled into our quality system and addressed promptly.


